Securing Artificial-Intelligence Systems
The methods underpinning the production machine learning systems are systematically vulnerable to a new class of vulnerabilities across…
The methods underpinning the production machine learning systems are systematically vulnerable to a new class of vulnerabilities across…
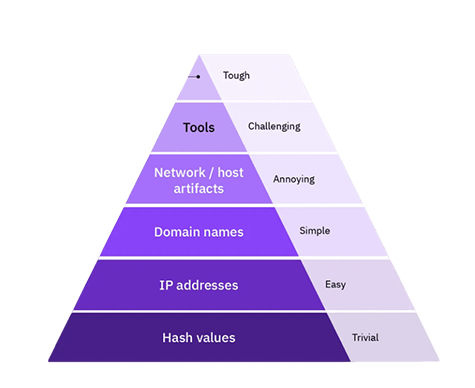
The “Pyramid of Pain” is a cybersecurity concept that suggests that the more layers of an organization’s defenses…
The Time-to-Compromise (TTC) metric is a useful tool for estimating the risk of cyber attacks and determining the…
The evolution of graphs and attack trees has played a significant role in the field of cybersecurity. These…
Cognitive bias is a natural human phenomenon that occurs when we make judgments or decisions based on our…
STIX (Structured Threat Information eXpression) and TAXII (Trusted Automated Exchange of Indicator Information) are two important standards in…
Measuring the severity of a cyber threat can be a challenging task, as it involves evaluating the potential…
Mobile devices share some architectural similarities with their desktop counterparts, but there are significant distinctions between personal computers…
The MITRE ATT&CK framework is a widely-used resource for understanding and mitigating cyber threats. It is a comprehensive…
Threat modeling is a crucial part of the software development process, but it’s not just for developers. In…